 How a VPN (Virtual Private Network) Works
How a VPN (Virtual Private Network) Works
A VPN connection to a business's main office can help its employees be productive when they're on the go. Each group member of your network can communicate in a secure and reliable, can accommodate more users & different locations much easier.
How Virtual Private Networks Work
A VPN connection to a business's main office can help its employees be productive when they're on the go.
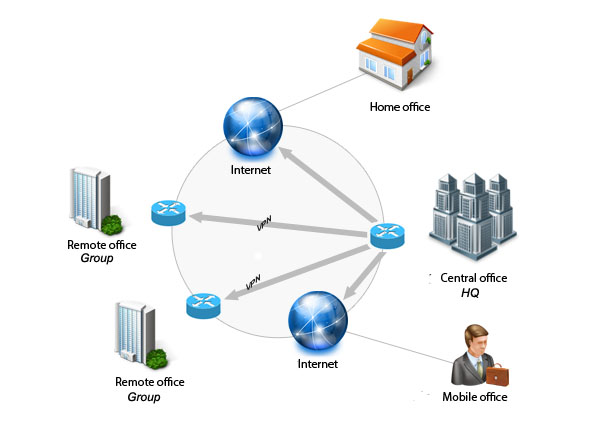
As a business grows such as Tuntex, it might expand to multiple workshops or offices across the country and around the world. But there is one thing that all companies need: a way to maintain fast, secure, and reliable communications wherever their offices are located. Traveling employees like salespeople, CEO (Chief Executive Officer), CTO (Chief Technical Officer), etc need an equally secure and reliable way to connect to their business's computer network from remote locations. Even while on leisure, people want to keep their computers safe when on an unfamiliar or unsecured network.
One popular technology to accomplish these goals is a VPN (virtual private network). A VPN is a private network that uses a public network (usually the internet) to connect remote sites (outside network) or users together. The VPN uses "virtual" connections routed through the internet from the business's private network or a third-party VPN service to the remote site, distant offices or person. VPNs help ensure security — anyone intercepting the encrypted data can't read it.
A typical VPN might have a main local-area network (LAN) at the corporate headquarters of a company, other LANs at remote offices or facilities, and individual users that connect from out in the field.
A VPN is a private network that uses a public network (usually the Internet) to connect remote sites or users together. Instead of using a dedicated, real-world connection, such as leased line, a VPN uses "virtual" connections routed through the Internet from the company's private network to the remote site or employee.
What Makes a VPN?¶
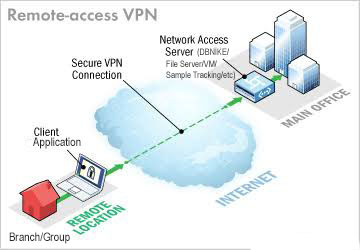
A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the internet. Site-to-site VPN extends the company's network, making computer resources from one location available to employees at other locations.
An example of a company that needs a site-to-site VPN is a growing corporation with dozens of branch offices around the world.
A well-designed VPN can greatly benefit a company. For example, it can:
-
Extend geographic connectivity
-
Reduce operational costs versus traditional WANs
-
Reduce transit times and traveling costs for remote users
-
Improve productivity
-
Simplify network topology
-
Provide global networking opportunities
-
Provide telecommuter support
-
Provide faster Return On Investment (ROI) than traditional WAN
What features are needed in a well-designed VPN? It should incorporate these items:
-
Security
-
Reliability
-
Scalability
-
Network Management
-
Policy Management
Analogy Each LAN is an IsLANd¶
Imagine that you live on an island in a huge ocean. There are thousands of other islands all around you, some very close and others farther away. The normal way to travel is to take a ferry from your island to whichever island you wish to visit. Traveling on a ferry means that you have almost no privacy. Anything you do can be seen by someone else.
Assume that each island represents a private LAN and the ocean is the Internet. Traveling by ferry is like connecting to a web server or to another device through the Internet. You have no control over the wires and routers that make up the Internet, just like you have no control over the other people on the ferry. This leaves you susceptible to security issues if you try to connect between two private networks using a public resource.
Your island decides to build a bridge to another island so that there is an easier, more secure and direct way for people to travel between the two. It is expensive to build and maintain the bridge, even though the island you are connecting with is very close. But the need for a reliable, secure path is so great that you do it anyway. Your island would like to connect to a second island that is much farther away, but you decide that it is too expensive.
This situation is very much like having a leased line. The bridges (leased lines) are separate from the ocean (Internet), yet they are able to connect the islands (LANs). Many companies have chosen this route because of the need for security and reliability in connecting their remote offices. However, if the offices are very far apart, the cost can be prohibitively high - just like trying to build a bridge that spans a great distance.
So how does VPN fit in to this analogy? We could give each inhabitant of our islands their own small submarine with these properties.
-
It is fast.
-
It is easy to take with you wherever you go.
-
It is able to completely hide you from any other boats or submarines.
-
It is dependable.
-
It costs little to add additional submarines to your fleet once the first is purchased.
Although they are traveling in the ocean along with other traffic, the inhabitants of our two islands could travel back and forth whenever they wanted to with privacy and security. That is essentially how a VPN works. Each remote member of your network can communicate in a secure and reliable manner using the Internet as the medium to connect to the private LAN. A VPN can grow to accommodate more users and different locations much easier. Moreover, the distance doesn't matter, because VPNs can easily connect multiple geographic locations worldwide.
Tuntex-SYS IT Div Originally Published: Feb 10, 2021
Sources¶
- Cisco. "How Virtual Private Networks Work." Oct. 13, 2008. (May 6, 2019)
- Friedl, Stephen J. "Steve Friedl's Unixwiz.net Tech Tips: An Illustrated Guide to IPSec." Aug. 24, 2005. (May 6, 2019)
- Microsoft. "TechNect: VPN Tunneling Protocols." 2011. (May 6, 2019)
- Pandya, Hiten M. "FreeBSD Handbook: Understanding IPSec." The FreeBSD Documentation Project. (May 6, 2019)
Comments